Features Overview and Roadmap¶
This page provides our roadmap and a high level overview of supported features. Please note that schedule and the content of versions may change without further notice.
Summary of supported and roadmap features¶
Feature |
Supported? |
|---|---|
Debian based installation |
✅ |
Zero-Touch Provisioning |
✅ |
Multi-Tenant Accounts and Users |
✅ |
Organization based inventory |
✅ |
IPSec over VxLAN tunnels |
✅ |
Flexible tunnel configuration: Full-Mesh, Hub & Spoke, Partial-Mesh |
✅ |
Tunnel quality metrics |
✅ |
Application Identification (L3/L4) |
✅ |
Multiple WAN/LAN interfaces |
✅ |
Application based path selection policy |
✅ |
Internet Breakout |
✅ |
DHCP server |
✅ |
Static routes configuration |
✅ |
Dynamic flexiEdge configuration changes |
✅ |
Monitoring & Dashboards |
✅ |
flexiEdge error detection and notifications |
✅ |
Credit card based billing |
✅ |
Scheduled auto software upgrade of flexiEdge |
✅ |
Northbound REST API and access keys |
✅ |
Troubleshooting improvements |
✅ |
WAN side DHCP |
✅ |
Devices handling and viewing improvements |
✅ |
More NAT Traversal options, including single-side symmetric NAT traversal |
✅ |
Monitoring enhancements |
✅ |
Additional, non-ethernet, interfaces (LTE, WiFi) |
✅ |
flexiEdge side APIs and UI |
✅ |
Security features |
✅ |
AI based Quality based routing (QBR) |
✅ |
IPSec Peering (e.g. Cloud Security, Network aggregation GWs) |
✅ |
AI based network healing |
✅ |
Performance and scale improvements |
✅ |
Network connectivity troubleshooting in flexiEdge Web UI |
✅ |
flexiEdge recovery scenarios |
✅ |
Multi language support |
✅ |
Enhanced Monitoring |
✅ |
PPPoE |
✅ |
Remote Worker Application |
✅ |
BGP support |
✅ |
Support flexiEdge in GCP |
✅ |
Kubernetes support with Kubevirt |
✅ |
QBR for DIA |
✅ |
Report Interfaces’ Link Status in flexiManage |
✅ |
Allow starting router IP/LTE failure |
✅ |
Advanced QoS |
✅ |
Error handling simplification |
✅ |
2FA Login |
✅ |
VLAN (802.1Q) |
✅ |
flexiEdge High Availability - VRRP |
✅ |
Notification improvements |
✅ |
LAN side NAT |
✅ |
Role based access keys |
✅ |
Advanced routing and conditional static routes |
✅ |
Device templating |
On-Going |
Wizards and Installation simplification |
On-Going |
Diversion to Linux applications |
On-Going |
QBR Measurement Improvement |
On-Going |
Netflow support |
On-Going |
Network Analytics |
On-Going |
Segmentation (VRF) |
On-Going |
Additional applications and application framework |
On-Going |
More enhancements based on customer input and priorities |
On-Going |
Feature Description¶
flexiEdge Installation¶
The flexiEdge software is a debian package installed on Ubuntu 18.04 LTS. The flexiEdge software can be installed on various architectures such as:
Bare-metal hardware
Virtual Machine, supported hypervisors are KVM, VMware and VirtualBox.
AWS EC2 and Hetzner VPS
Support for additional installation environments will be prioritized and added based on user feedback
Since the installation comes as a package, it allows installation on a customized Ubuntu. The installation adds all the necessary components required for running the flexiEdge router including VPP, FRR, and flexiWAN Agent. All components are installed as Ubuntu systemd services.
On installation, the software performs various system checks for both Hardware and Software configuration. The system checker allows to fix Software configuration issues but does not block the service from running.
The agent provides various CLI commands for troubleshooting such as starting, stopping, resetting, and showing of information.
For more information, please refer to the flexiEdge Installation section in the documentation menu on the left.
Zero-Touch Provisioning¶
The flexiEdge connects with flexiManage using a token created in flexiManage. Only one token is required for all flexiEdge devices of the organization. The Token is placed in a specific file in flexiEdge and can be copied to all flexiEdge devices. On registration, the flexiEdge device automatically gets a unique, per-device token, and use it for its connection and authentication with flexiManage. A pre-defined image that contain the organization token, will register automatically without further interaction required by the user (Zero Touch Provisioning).
To prevent the connection of non-permitted devices with flexiManage and the organization’s network, the device must be explicitly approved on flexiManage after registration. Once approved, the flexiEdge device connects to flexiManage and is fully operational and manageable by flexiManage.
Multi-Tenant Accounts and Users¶
flexiManage is a multi-tenant, multi-user and multi-organization system. This allows for hierarchy between organizations in the account. A typical use of the multi-tenant capability will be for an MSP, SI or VAR to create in his account an organization for each of his enterprise customers while managing them from one central location and account (single login). It is important to note that each organization has its own Devices inventory and network. The network of each organization (e.g. enterprise) is isolated and one organization can’t access the network of the other organization.
Every user has access permission to various account resources. Users at an account level and organization level can invite other users with the same rights or less.
Refer to Account and Users Management page for additional information.
Organization Network Inventory¶
Each organization has an inventory that contains flexiEdge devices, tunnels, tokens, path labels, and application identification. Network operations are done at the organization level. For security reasons, each organization is isolated in terms of the inventory and it is not possible to create tunnels between networks of different organizations, however users with account or group access can view and operate different organizations under the account or group to which they have access permissions to.
Devices¶
Every registered flexiEdge device is shown in flexiManage with its status. flexiManage collects information for every connected flexiEdge device. The information includes general configuration parameters, interfaces, monitored statistics and health, routes, device logs and internal configuration. Device configuration can be dynamically changed while the device is running.
Tunnels¶
flexiWAN supports IPSec over VxLAN tunnels. The tunnel structure is shown in the figure below:
![@startuml
skinparam defaultTextAlignment center
rectangle PKT [
VxLAN + UDP
--
IPSec Tunnel
--
GRE
--
Original Packet
]
@enduml](../_images/plantuml-c47d3989cae71374c00fe2372e943022e9ae5b1f.png)
The tunnels are connected through the WAN interface, where LAN subnets are learned across the tunnels using OSPF. Every tunnel is created between two flexiEdge devices using loopback interfaces (one per router) in the subnet range of 10.100.X.Y/31. Internally, subnet 10.101.X.Y is also used. As shown in the next figure, in order to send packet to a given tunnel, the traffic is routed to the tunnel next hop which is the loopback address of the other tunnel side. Packets going through the tunnel do not pass NAT and use VxLAN UDP ports 4789 for both tunnel sides.
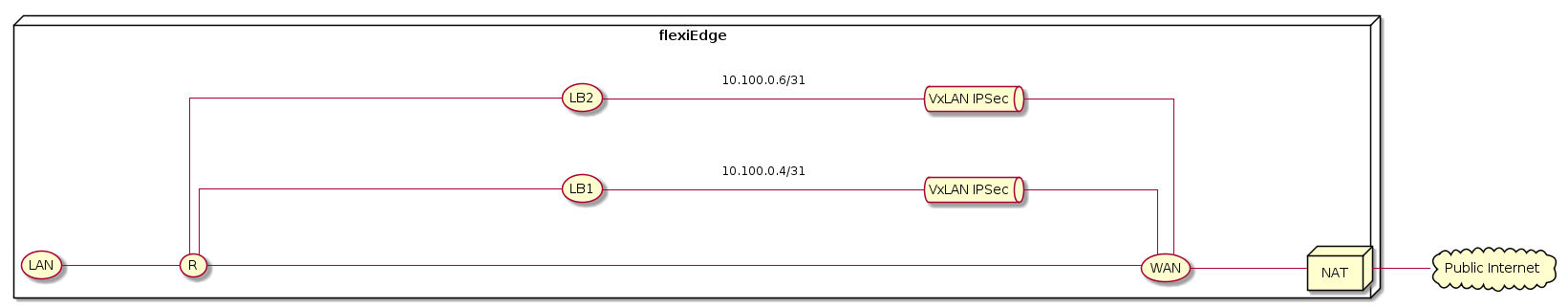
The system supports flexible tunnel configuration such as full mesh, hub and spoke or any other combination. Tunnels are easily created by selecting devices and adding tunnels. Full mesh tunnels will be created across all selected devices.
For Pre-Shared Key method, the tunnel IPSec parameters are:
IPSec Protocol: ESP
IPSec Mode: Tunnel mode
Crypto Algorithm: AES-CBC-128
Integrity Algorithm: SHA-256-128
For IKEv2 method, parameters are:
Crypto Algorithm: AESCBC
Integrity Algorithm: HMAC-SHA2-256-128
DH-Group: modp-2048
Key size: 256
flexiWAN measures connectivity, latency and loss across the tunnel end-points. Every flexiEdge runs ICMP echo request every second and measure the round trip time (RTT) and loss based on these packets. If any path exists between the two end-points, the tunnel status will presented as connected.
Path labels¶
Path labels offer a powerful way to organize networks and tunnels in flexiWAN. Path labels define unique underlay networks scheme where each label represent a separate logical underlay networks.
Application Identification¶
The flexiEdge devices have the capability to identify network applications based on IP and Ports. Occasionally, a flexiWAN cloud service generates a list of rules and categorization for every network application. This list is read by every flexiManage instance and is pushed to the flexiEdge devices it manages. The administrator can define new applications specific for the organization or modify the categorizations of the provided applications. The applications are then used for traffic classification in various policies (such as Path Selection).
Refer to Application Identification page for additional information.
Multiple WAN/LAN interfaces¶
flexiEdge supports multiple WAN/LAN access interfaces and a different gateway for every interface. An application based policy is used to select the outgoing WAN interface for a given application.
Application based Path Selection policy¶
Path Selection policy enables application based routing in flexiWAN. With Path Selection and its policies, users can decide through which WAN interface certain traffic is routed. It also brings load balancing, redundancy, traffic differentiation and blocking of applications.
Refer to Path Selection Policy page for additional information.
Application based Quality of Service (QoS) policy¶
QoS policy enables prioritization of specific types of traffic and ensure that real-time or important applications continue operating and not being blocked by lower priority applications. Every application is mapped to one of 5 queues based on its service class and priority. The total interface bandwidth and percentage per queue can be set using the QoS policy. flexiWAN supports a global QoS policy per flexiEdge device or different policy per interface.
Refer to Quality of Service page for additional information.
Security firewall¶
Built with SDWAN and SASE concepts in mind, to be deployed at scale with ease, flexiWAN firewall functionality offers flexible control to filter certain or all traffic based on several criterias, including Application Identifications, while still offering traditional firewall features such as rules, port forwarding and 1:1 NAT.
Refer to Firewall page for additional information.
Internet Breakout¶
Any flexiEdge device allows to send traffic directly to the Public Internet without going via the tunnel. Any traffic that goes to the Public Internet passes through NAT in order to hide the internal network (LAN) IP addresses.
The selection of Public Internet or Tunnel is based on routing. In a typical deployment, the internal network / LAN are accessible via the tunnel and any other traffic is routed via the default gateway which points to the Public Internet. This default behavior could be modified using static routes. Refer to the routing page for more information on how to define static routes
NAT Traversal¶
NAT traversal is the ability to create tunnels when the traffic passes through NAT.
NAT traversal is supported for:
Public IP and Port learning using STUN (default)
Adjust Public IP and Port when one of the sides behind a Symmetric NAT or CGNAT
1:1 NAT (such as DMZ or AWS elastic IP)
Using port forwarding on the access device (for the VxLAN port 4789)
The STUN mode allows to create a tunnel even when the flexiEdge device is located behind an access device and NAT. On the creation of the VxLAN tunnel, each flexiEdge device opens a NAT pinhole throught the access router to the other device using STUN and learns the public IP and port. The tunnel is created using the learned IP and port.
DHCP server¶
flexiEdge devices support DHCP server configuration per device. The DHCP server allows for LAN side end-points to auto connect to the device and get its IP and DNS server. The DHCP server supports static MAC based lease.
Static Routes¶
In some environments specific subnets are not learned by routing protocols. flexiManage allows to define static routes per device to route specific subnets to a desired interface and gateway.
Refer to routing page for additional information.
Monitoring & Dashboards¶
flexiManage collects statistics per device and shows the bits per second (BPS) or packets per second (PPS) per device (in the device info page) or for the entire network (in the dashboard)
The dashboard on flexiManage presents the following information:
The network connectivity and status of each tunnel
The total network bandwidgh and packets per second
The device page presents network bandwidth and packets per second per device
Notifications¶
flexiManage collect events from the network and generate notifications. Notifications are measured when:
A new software is available and the device is running an old software
When a device disconnected from flexiManage
When the router stopped running
When the tunnel round trip time is high (larger than 100 milliseconds)
When the drop rate is high (larger than 50%)
If there are unread notifications, the account owners gets an email once a day. Notifications can be marked as read and the email can be disabled from the account profile page.
Refer to System Notification page for additional information.
Billing¶
When opening a free account on flexiManage, the account is put on a trial period for 30 days. During the trial period support is provided and we are happy to assist with installation and configuration as we see required. Once the trial is over, the user is required to add a valid method of payment to the system. flexiManage does not store any credit card information and all the billing transactions occurs via a secure, 3rd party billing system. Every account is charged monthly by the maximum concurrent flexiEdge devices registered to the system. The pricing is per registered device regardless of the bandwidth transmitted through that device. The price per device varies based on the number of registered devices and could be seen in the flexiWAN pricing page. The billing is done in the account level and any billing information is accessible only to the account owners.
Refer to Billing System page for additional information.
Software Auto Upgrade¶
flexiWAN release flexiEdge software updates regularly. These updates include new features and bug fixes. The account owners receives an email with the release update. A notification is shown in flexiManage for devices that require upgrade. flexiManage support backwards compatibility of one major release, devices older than one major release will not be able to connect with flexiManage. Therefore it is recommended to regularly upgrade the devices to the latest release. Upgrade can be done immediately, on a scheduled window or, if not selected, flexiManage will upgrade the device automatically at the date specified as last day for upgrade.
Refer to Software Auto Upgrade page for additional information.
flexiManage and flexiEdge configuration synchronization¶
flexiManage is the single source of truth, any user or REST configuration is executed with no blocking. When a configuration change required on the flexiEdge device, a job is created which is sent based on its priority. flexiManage makes sure to synchronize the flexiEdge device with the desired configuration and show the device in ‘sync’ status
Northbound API¶
flexiManage operations can be done via the flexiWAN UI. flexiManage also supports REST based Northbound API to manage and provision the networks.
Refer to Software Auto Upgrade page for additional information.
Troubleshooting¶
flexiManage provides various troubleshooting capabilities such as show device logs, packet traces, monitor jobs sent to every device
DHCP Client¶
Allow to provision DHCP client for WAN interfaces. The DHCP client detects an IP change and provisions the relevant tunnels in the network to use the new IP address. This allows to dynamically allocate IPs or move devices between locations and maintain the same network connectivity.
High Availability¶
Multiple flexiEdge devices can work in Active:Standby or Active:Aactive mode where traffic from the LAN is load-balanced between them. Each flexiEdge can have multiple WAN interfaces, and each WAN interface can have multiple tunnels to the same or multiple destinations. A failure of a flexiEdge device will route all traffic through the healthy device and can still load-balance traffic to multiple tunnels and destination flexiEdges. From release 6.3.X, we support VRRP (Virtual Router Redundancy Protocol) where one or more physical flexiEdge devices can form a virtual or logical router. With VRRP, a client host connects to a virtual IP physcially connected to one of the flexiEdge devcies in the VRRP group. For more information, please refer to the High Availability page.
LTE Module¶
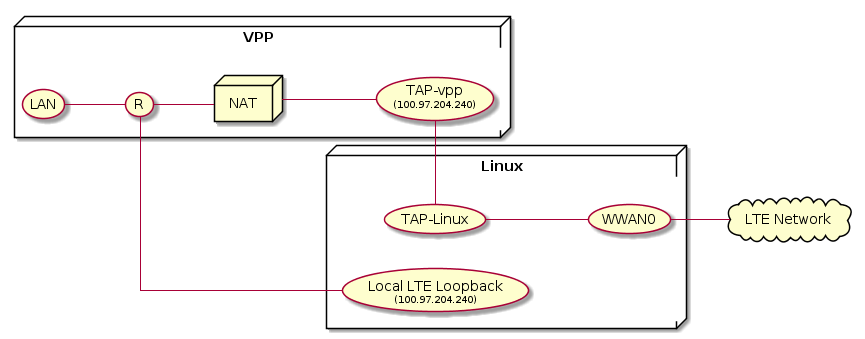
LTE interfaces are not DPDK based and therefore requires a unique connectivity. The LTE device is owned and handled by Linux but connected using a tap interface to VPP for executing the routing and services. The next diagram shows a sketch of the connectivity. Traffic to/from LTE goes between the tap interfaces of Linux and VPP and to the LTE device converting between L2 and L3 packets. This way all flexiWAN features are supported for LTE interfaces as for any other DPDK interface.
WiFi Module¶
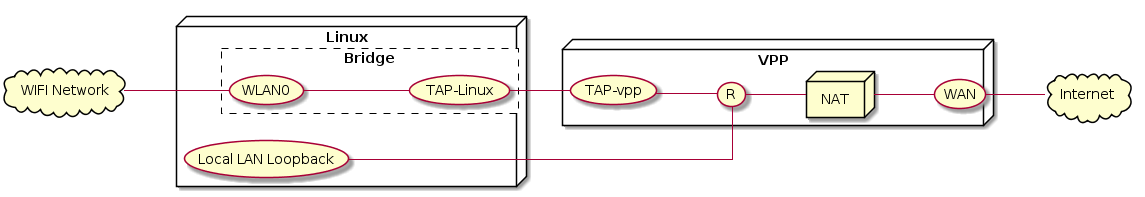
Similar to LTE, WiFi devices are owned and processed by Linux and connected using a tap interface to VPP. The WiFi interface is connected via bridge to the Linux tap.
AI based Quality Based Routing (QBR)¶
AI based Quality Based Routing (QBR) enhances the path selection policy by routing traffic dynamically to the best available link. For a given application or application categories (e.g. category, importance and service-class), the system measures the loss and latency per tunnel and decides which tunnel would be best to route the application on in order to meet the application network quality requirements. The system will try to balance the applications across the links to utilize the available links in the best way. QBR is selected by application or application categories in the path selection policy.
IPsec Peering¶
Peer connection allows to provision a pure IPSec tunnel from flexiEdge device to another peer. This capability can be used for a large variety of use cases, here are a few examples:
Cloud Security - connecting to cloud security services or SASE services. Service for multiple providers can be provisioned in parallel.
Network aggregation gateways
Connecting to cloud
Connecting tunnels to non flexiEdge devices
The same path selection policies are applied to peer connections for traffic from flexiEdge. It is possible to select which application to send to each tunnel or peer. By policy the administrator has the flexibility to decide which traffic is sent directly between sites, which traffic goes to local breakout (DIA) and which traffic goes through the cloud security service.
Using a peer connection instead of using a flexiWAN tunnels does have some drawbacks:
Since flexiManage does not control the peers, connecting to a peer requires more configuration from the administrator
Traffic back from the peer to flexiEdge does not benefit from the SD-WAN advantages available on flexiEdge as the remote peer sending the traffic is not a flexiEdge instance but rather an IPsec peer
AI-based network healing¶
flexiEdge and flexiManage work in harmony to detect network changes, fix possible issues and provide configuration recommendations:
Fix issues, if possible, without the need for administrator intervention
Suggest recommended configuration changes to better optimize the network
LAN NAT¶
From release 6.3.X, we support defining LAN side 1:1 NAT. This can be used to rewrite the source address from the LAN network and/or the destination address for the outgoing traffic to either the Internet or tunnel paths. This allows to have the same subnet on multiple devices while still representing them uniquely in the network or replacing the destination for the outgoing packet. For more information, please check the LAN NAT page.
Notifications & Alerts¶
flexiWAN supports granular notification on various network events such as disconnections, performance degradation, high resource usage and more. It is allowed to define the criticality of every notification, when to inform about it on email or webhooks and thresholds. The system can easily show the active notifications in the network and allow to modify it. In addition it’s possible to get a daily report for all notifications which occured on the network during the last day.