IPsec Peering¶
Overview¶
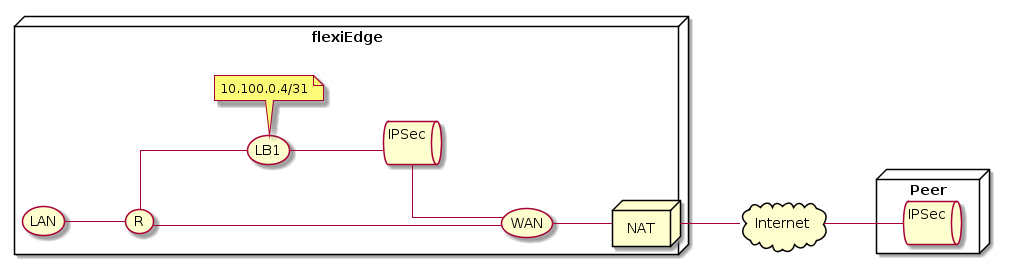
The IPsec Peering feature allows connecting pure IPSec tunnels between flexiEdge devices to other peers.
This capability can be used for a large variety of use cases, here are a few examples:
Cloud Security - connecting to cloud security services or SASE services. Service for multiple providers can be provisioned in parallel.
Network aggregation gateways
Connecting to cloud
Connecting tunnels to non flexiEdge devices
IPsec Peering establishes connections using IKEv2/IPSec, so any 3rd party devices or services that can match the parameters, should be able to establish tunnels with flexiEdge devices. The flexiWAN IPsec Peering implementation supports both routed and policy based connections.
The same path selection policies are applied to peer connections for traffic from flexiEdge. It is possible to select which application to send to each tunnel or peer. By policy the administrator has the flexibility to decide which traffic is sent directly between sites, which traffic goes to local breakout (DIA) and which traffic goes through the cloud security service.
Peering IKEv2/IPsec implementation uses the following ports:
- UDP
4500 and 500
- ESP
50
Note
Using a peer connection instead of using a flexiWAN tunnels does have some drawbacks:
Since flexiManage does not control the peers, connecting to a peer requires more configuration from the administrator
Traffic back from the peer to flexiEdge does not benefit from the SD-WAN advantages available on flexiEdge as the remote peer sending the traffic is not a flexiEdge instance but rather an IPsec peer
Configuring a new IPsec peer¶
IPsec Peering functionality can be accessed from Inventory > Peers.
Click on New Peer button to get started.
In order to add a new peer, fill out the following areas:
- Name
Peer name for e.g. “Company router”
- ID Type
Define identification type. Can be a Fully Qualified Domain Name or IP address based.
- Local ID
Enter distinguished name for local identifier. If IPv4 is selected under type above, keep automatic instead.
- Remote ID
Define remote IP or distinguished name.
- PSK
Pre-Shared Key used for authentication on both ends. Make sure to use a strong key for better security.
- Remote IP
IP address of remote IPsec site to which flexiEdge will connect.
Peer Monitoring¶
Define a monitor IP or URL used for monitoring Peer connectivity. IP and URL based monitoring can be single or multiple comma entries. Monitoring traffic will exit using the Peer as gateway, so any IP or URL may be configured.
Warning
If the monitoring IP is not defined peer connection latency and drop rate will not be measured.
Cryptography¶
In this section all authentication and key exchange parameters can be set. Make sure to use a matching parameters on both sides. IPsec Peering relies on Internet Key Exchange v2 and Encapsulating Security Payload (ESP) protocols. We suggest to use and match these defaults on the remote end.
Traffic Selector¶
In the last section, Traffic Selector, configure local and remote traffic ranges which will be allowed to communicate. If kept as default, communication from all ranges will be allowed.
Peer Path Label¶
Once new Peer is added, before connecting to it, the next step is to create a tunnel Path Label which will be used for deploying the new Peering connection. The following steps are required on flexiEdge device site before adding a new peering connection:
Creating a new tunnel Path Label dedicated for Peering connection.
Assigning the newly created Path Label to the WAN interface on the flexiEdge device.
Navigate to Inventory > Path Labels and create a new Path Label which will be used for Peering. Make sure DIA (internet breakout) is not selected. Check Path Labels documentation section to learn more about path labels.
After creating the Path Label, navigate to the device on which Peering connection will be deployed. Assign the newly created Path Label to WAN interface. On a device with multiple WAN interfaces Peering connection will use the WAN interface Path Label is assigned to.
Creating a peer connection¶
Adding a peer connection to an existing flexiEdge site is done in just a few clicks. Navigate to Inventory > Devices, select the device to which the Path Label was assigned and click on the Action menu. Select Create Peer Connection from the menu.
From the Create Peers dialog select the previously created Path Label and select the Peer configuration. Click Create Peer.
Advanced section offers OSPF cost and routig options. New peers use OSPF routing by default however BGP can be used instead.
That’s it, the new Peer connection should be created and connecting. You can define any routing or path selection policies for peers as for regular tunnels.
Viewing or removing peer connections¶
After adding a peering connection, its status can be viewed from Inventory > Tunnels, together with other tunnels that may exist.
In this case, CloudVPC interface is identified as Peer. If latency and drop rate are not shown, make sure to add the Monitor IP in peering configuration.
Deleting a peer connection is done in the same way as with tunnels, simply click on delete icon under action column and confirm the deletion.
Deployment¶
The flexiWAN IPsec Peering functionality has been tested with multiple Cloud providers and 3rd party network devices. We are continously working on adding more supported providers and devices. Below listed are tested and supported providers, however any 3rd party devices or services with matching IKEv2/IPsec parameters should be able to establish connection using flexiWAN peering.
Peering feature has been tested and confirmed to work with the following cloud providers and 3rd party networking vendors:
Amazon Site-to-Site VPN https://aws.amazon.com/vpn/site-to-site-vpn/
Acreto Gateway https://kb.acreto.net/how-to/quickstart/create-gateway/
Oracle Site-to-Site VPN https://docs.oracle.com/en-us/iaas/Content/Network/Tasks/overviewIPsec.htm
strongSwan
Meraki Site-to-Site VPN https://documentation.meraki.com/MX/Site-to-site_VPN/Site-to-Site_VPN_Settings#Non-Meraki_VPN_peers
pfSense IKEv2/IPsec VTI
Cisco VTI
Troubleshooting¶
To view status of peer connections enter the following command from the device Command tab or using shell:
vppctl show ikev2 sa details
Advanced logging may be set running the following commands via Command tab or shell:
vppctl ikev2 set logging level 5vppctl event-logger clearvppctl show event-logger
After entering the above commands, IKEv2/IPsec logging will be outputed to the device syslog. Syslog can be fetched from flexiManage, by navigating to device Logs tab.