Remote Worker VPN¶
About¶
Remote Worker VPN application improves core flexiWAN functionality by introducing remote access to company resources. IT admins can add the Remote Worker PVN application to their Organization from the flexiWAN AppStore in flexiManage and centrally configure and manage it from flexiManage. When installed on a flexiEdge devices, the application introduces VPN server functionality to it.
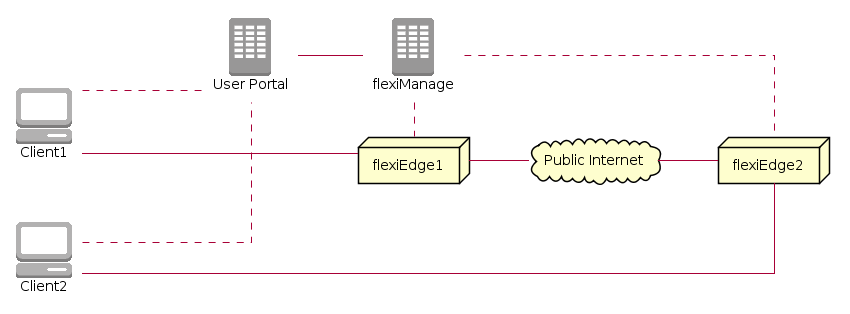
How does it work¶
Remote Worker VPN comprises the following components:
Application configuration accessible from App Store > Installed > Remote Worker VPN. Deployment is possible on a single or multiple flexiEdge. If installed on multiple flexiEdge devices, end users will be automatically connected to the nearest site to their geographic location.
Remote Worker Workspace portal page from where end-users can access resources required for VPN access. Multiple authentication methods for remote users are available, including Google Workspace and Azure. It is also possible to authenticate using flexiManage credentials (typically for IT testing and POC).
Remote Worker client software used for establishing VPN connections from remote devices
For the remote users to successfully use Remote Worker VPN, configuration is required from flexiManage. Once the application is configured and deployed on a single or multiple flexiEdge sites, end-users can access the Workspace portal to download the flexiWAN VPN application. Afterwards end-users can use the VPN application from their own computers to access internal resources.
For more details, follow the deployment and configurations steps below.
Requirements¶
Starting from release 5.2.X, every flexiEdge device should be able to run the Remote Worker VPN. Client and server VPN performance will vary based on device hardware specifications.
Installation¶
The Remote Worker VPN application can be installed by navigating to the App Store on the flexiManage sidebar and clicking on Available section. From there, simply click on the install icon and confirm your choice.
Once the application is installed, click the Open button to access the Remote Worker VPN configuration and settings page.
Configuration¶
About¶
Remote Worker VPN can be configured from App Store > Installed applications section in sidebar. Click on the yellow settings icon to access configuration page.
Configuration settings are divided into Server configuration and Authentication methods.
Server Configuration¶
- Workspace name
Unique identifier of your organization, used for the Remote Worker portal.
- Portal access link
Sharable link for remote users to log in and access VPN resources.
- Max Remote Worker Users
Number of unique users which can login to workspace on a organizational level during a billing period. Three users are allowed to login for free per account in the billing period which is the sum of max remote users for all organizations under the account. To increase the license number, please contact yourfriends@flexiwan.com.
- Server port
Port used for VPN server, default is 1194. A firewall rule is added to flexiEdge device when application is installed.
- Route all client traffic over VPN
Forces all client traffic across VPN tunnel, using nearest flexiEdge for internet access.
- DNS IP’s and domains
Define which DNS servers will remote devices use for domain name resolution.
The following screenshot shows correctly populated server settings:
Authentication methods¶
The Remote Worker VPN supports several methods for end user authentication with the Remote Worker Portal.
Google Workspace
Allows Google Workspace / Google Apps for end user authentication. Supports multiple domains via the add option. By default only Domain name column is required, while other columns can be left blank. In this case all users from listed domain will be able to authenticate using their Google Workspace account.
Other fields are required only in case when specific user groups should be allowed to authenticate. For this use case, additional configuration must be made from Google Workspace. Specifically it is necessary to create an IAM service account on Google Workspace so flexiWAN backend can access Admin Directory Group in read-only mode. Note, no private information is exposed to flexiWAN, we are querying only if the logged in user is member of a specified group.
Learn more about Google IAM here.
In order for remote users to successfully authenticate using this method, the following configuration options are available:
- Domain name
Enter domain name used for end user emails. Required field.
- Group membership
Limit authentication to only specific user groups. Supports multiple comma separated groups. Not required field, when not used all users from Google Workspace will be able to authenticate.
- Service Account
Google service account, only required when using specific groups.
- Private key
Private key issued by Google.
- Admin email
Google Workspace admin email address. Only used for verification, and not configuration / logging in.
Note
Private Google Mail accounts cannot be used with the Remote Worker VPN, only Google Workspace accounts are able to authenticate.
Azure AD
Allows Azure Active Directory for end user authentication. In order for remote users to successfully authenticate using this method, the following configuration options are available:
- Domain
Enter domain name used for end user emails. Required field.
- Groups
Limit authentication to only specific user groups. Supports multiple comma separated groups. Not required, when not used all users from Azure Active Directory will be able to authenticate.
Note, after enabling and configuring Azure Active Directory authentication method, AD administrator must attempt to authenticate first before end users. This is in order to consent authentication to Azure AD from the Remote Worker VPN. Note, no login or private information is handled by flexiWAN side.
flexiManage
Use flexiManage accounts to authenticate with the Remote Worker VPN end users. Please note, this feature is only for testing purposes and we do not recommend to utilize flexiManage for authentication in production.
Simply enable the authentication and provide remote users the link for portal authentication. Note, flexiManage portal link is different from the Workspace portal used with Google and Azure authentication.
Deployment¶
After configuring the Remote Worker VPN and at least one authentication method is enabled, the next step is to deploy it to a flexiEdge device. The application can be deployed on a single or multiple flexiEdge devices.
Deployment follows the usual flexiWAN deployment flow, select one or more devices and from the actions menu click on Install application.
From the drop down menu, select the Remote worker VPN application and confirm.
Final configuration step requires setting IP range which remote clients will use and limiting number of clients allowed to connect per flexiEdge. Note, total number of clients allowed is defined via the Remote Worker VPN configuration.
After clicking on save a job is sent to the device and in a few moments Remote Worker VPN will be deployed.
Workspace Portal¶
How it works¶
A Workspace portal is a dedicated location where end users can log in using an URL unique to their organization and download the VPN software required for accessing company resources. Each organization can have its own URL, which is configurable from the Remote Worker VPN configuration settings.
Workspace portal offers Remote Client VPN applications for remote users to install on their devices in order to access company resources. The client application includes two segments: OpenVPN client application and flexiWAN Workspace portal authentication wrapper.
The OpenVPN client by itself cannot authenticate with any flexiEdge, instead users always log in to the Remote Worker portal using Google Workspace, Azure AD or flexiManage authentication after which a secondary authentication for VPN session will occur. Workspace portal generates time sensitive token for actual device authentication and automatically opens OpenVPN client to authenticate to the nearest flexiEdge using the provided token. This process happens without user interaction in the background, users are only required to log in to portal and click on Launch Client.
Accessing Portal¶
In order share the workspace portal URL with your end users, first configure the Remote Worker VPN, then share the portal access link available from the settings.
Remote users can access the portal from the defined URL, after which they are required to authenticate using one of the set auth methods.
After authenticating using Google Workspace or Azure AD credentials, remote users can access company resources, in this case the Remote Worker VPN application which automatically downloads. Please see below section regarding client installation.
Optionally and for testing purposes, it’s possible to authenticate to portal using flexiManage account.
Remote Worker clients¶
The Remote Worker portal provides downloads of the Remote Worker clients which offer a VPN client for the remote workers to install and then connect to nearest flexiEdge. Please note, while the Remote Worker portal relies on the OpenVPN client, using standalone version directly from OpenVPN website will not work with the portal.
Currently, the Remote Worker portal offers VPN clients downloads for the following operating systems:
Windows - Supported OS’s are Windows 10 and 11. However older versions may work as well.
MacOS - Supported from Mojave to Monterey.
Installing client on Windows
After authenticating with the Remote Worker portal, client software will automatically automatically start to download.
Navigate to the download folder and locate the RemoteWorkerClient-1.0.0.exe file and run it to start the installation. Note, client versions numbers may change.
In a few moments the installer will install OpenVPN client software and flexiWAN connector for the Remote Worker VPN portal authentication. Upon installation completion click finish.
Navigate back to the the Remote Worker portal and click on Launch Client or simply refresh the page, after which the browser will ask to allow opening the Remote Worker Client application from it. To speed up authentication make sure to check always allow option and click on Open Link to launch the client.
The client will open and automatically start to connect to the nearest flexiEdge site based on client location. In a few moments a pop-up will display showing the remote user device is now connected.
That’s it, users can now access internal resources. It is recommended to use firewall rules and policies on flexiEdge sites to limit or allow access of remote user ranges. Finally, users can view connection status by opening OpenVPN application either from tray or desktop.
Trademarks¶
OpenVPN is a registered trademark of OpenVPN, Inc.